| Supported Versions |
|---|
| Firepower Device Manager(FDM) 6.7 |
| Firepower Management Center(FMC) 6.1 |
Introduction
Cisco Firepower Threat Defense is an integrative software image combining Cisco ASA and Firepower features into one hardware and software inclusive system.
The Cisco Firepower NGIPS is a next generation intrusion prevention system that shares a management console with the Cisco firewall offerings, called the Firepower Management Center.
Cisco ASA Firepower Services provides the following key capabilities:
Access control: This policy based capability allows a network security administrator to define, inspect, and log the traffic that traverses a firewall. Access control policies determine how traffic is permitted or denied in a network. For instance, you can configure a default action to inspect all traffic or block or trust all traffic without further inspection. You can achieve a more complete access control policy with enrichment data based on security threat intelligence. Whether you configure simple or complex rules, you can control traffic based on security zones, network or geographical locations, ports, applications, requested URLs, and per user.
Intrusion detection and prevention: Intrusion detection and prevention help you detect attempts from an attacker to gain unauthorized access to a network or host, create performance degradation, or steal information. You define intrusion detection and prevention policies based on your access control policies. Create and tune custom policies at a very granular level to specify how traffic is inspected in a network.
AMP and file control: You can detect, track, capture, analyze, and optionally block the transmission of files, including malware files and nested files inside archive files in network traffic. File control enables you to detect and block users from sending or receiving files of different specific types over a multitude of application protocols. You can configure file control as part of the overall access control policies and application inspection.
Application programming interfaces (APIs): Cisco ASA Firepower Services supports several ways to interact with the system using APIs.
Pre-Requisites
The OpsRamp Gateway must be installed.
Configure and install the integration
- Go to Setup > Integrations and Apps.
- Click + ADD on the INSTALLED APP page. The AVAILABLE APPS page displays all the available applications along with the newly created application with the version.
Notes:- If there are already installed applications, it will redirect to the INSTALLED APPS page, where all the installed applications are displayed.
- If there are no installed applications, it will navigate to the ADD APP page.
- You can even search for the application using the search option available. Also you can use the All Categories option to search.
- Click ADD in the Cisco Firepower Threat Defense application.
- Select an existing registered profile, and click Next.
- In the Configurations page, click + ADD. The Add Configuration page appears.
- Enter the below mentioned BASIC INFORMATION:
| Funtionality | Description |
|---|---|
| Name | Enter the name for the configuration. |
| IP Address/Host Name | IP address/host name of the target. |
| Port | Port Note: By default 443 is added. |
| Managed By | Select Managed By from the drop-down list. Note: As of now the application only supports discovery and monitoring for FTDs managed by: - Firepower management Center (FMC) - Firepower device manager (FDM) |
| Credentials | Select the credentials from the drop-down list. Note: Click + Add to create a credential. |
Notes:
- By default the Is Secure checkbox is selected.
Select the following:
- App Failure Notifications: if turned on, you will be notified in case of an application failure that is, Connectivity Exception, Authentication Exception.
- Alert Configuration: map alert configuration for third party alerts into OpsRamp.
- Below are the default values set for:
- Alert Severity: possible values of Alert Severity filter configuration property are “RED”,“YELLOW”.
- Alert Severity Mapping: possible values of Alert Severity Mapping filter configuration property are “RED”:“Critical”,“YELLOW”:“Warning”.
In the RESOURCE TYPE section, select:
- ALL: All the existing and future resources will be discovered.
- SELECT: You can select one or multiple resources to be discovered.
In the DISCOVERY SCHEDULE section, select Recurrence Pattern to add one of the following patterns:
- Minutes
- Hourly
- Daily
- Weekly
- Monthly
Click ADD.
Now the configuration is saved and displayed on the configurations page after you save it. From the same page, you may Edit and Remove the created configuration.
Click Finish.
The application is now installed and displayed on the Installed Integration page. Use the search field to find the installed application.
Modify the Configuration
See Modify an Installed Integration or Application article.
Note: Select the Cisco Firepower Threat Defense application.
View the Cisco Firepower Threat Defense device details
The Cisco Firepower Threat Defense application integration is displayed in the below navigation:
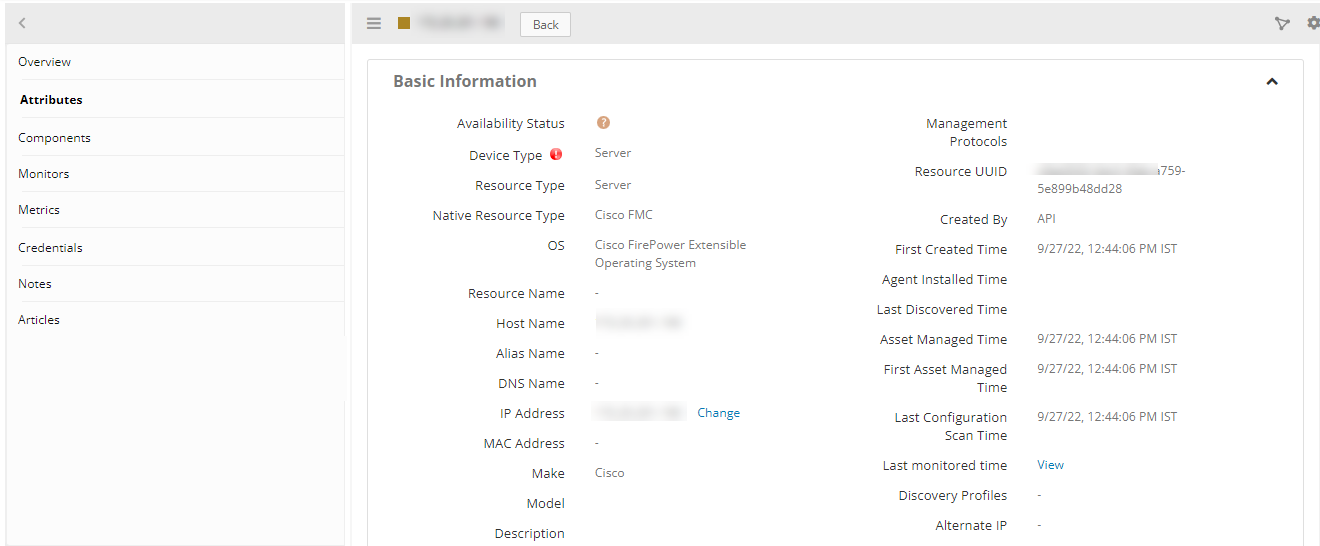
- FMC: Infrastructure > Resources > Server.
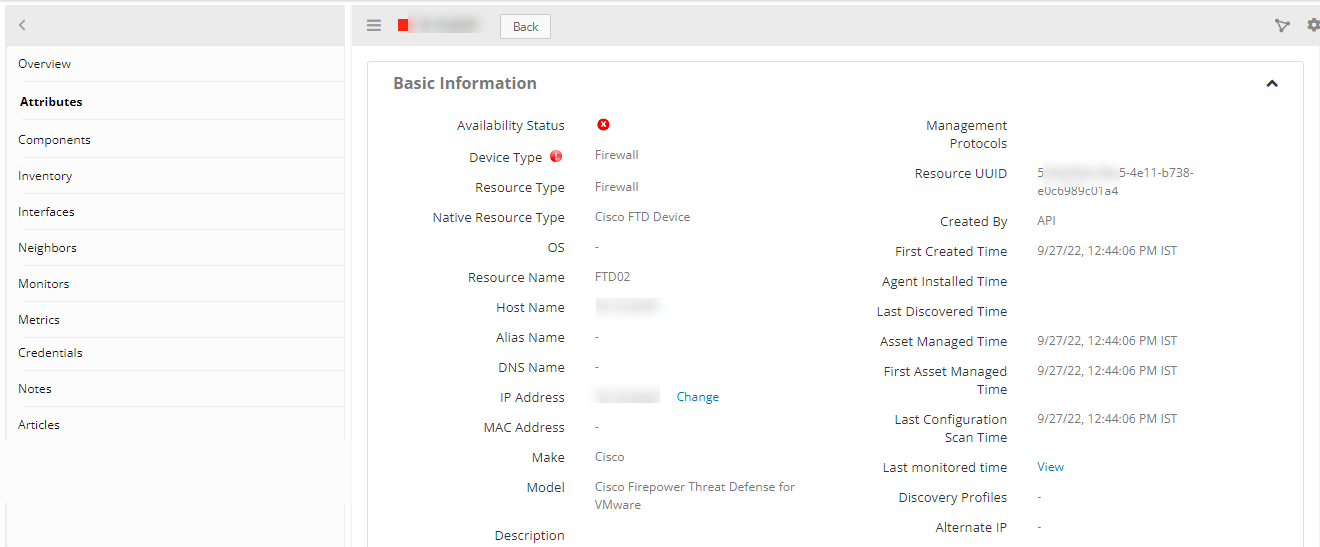
- FTD: Infrastructure > Resources > Network Device > Firewall.
Supported Metrics
| Metric Name | Unit | Description |
|---|---|---|
| cisco_ftd_health_status | Health status of Ftd device | |
| cisco_ftd_mem_free | Bytes | The total free memory. |
| mem_used | Bytes | The total memory available. |
| cisco_ftd_mem_used_percentage_lina | % | The percent of memory used by the data plane. |
| cisco_ftd_mem_used_percentage_snort | % | The percent of memory used by the Snort process. |
| cisco_ftd_mem_used_percentage_system_and_swap | % | The percent of memory used by the system and swap combined. |
| cisco_ftd_cpu_lina_cp_avg | % | The average CPU utilization for the control plane |
| cisco_ftd_cpu_lina_dp_avg | % | The average CPU utilization for the data plane. |
| cisco_ftd_cpu_snort_avg | % | The average CPU utilization for the Snort process. |
| cisco_ftd_cpu_system_avg | % | The average CPU utilization for the system processes. |
| cisco_ftd_cpu_lina_avg | % | The average CPU utilization for all the cores. |
| cisco_ftd_packets_bypassed_snort_busy | count | The number of packets that bypassed inspection when Snort was too busy to handle the packets. |
| cisco_ftd_packets_bypassed_snort_down | count | The number of packets that bypassed inspection when Snort was down. |
| cisco_ftd_packets_drops_rxq_full | count | The number of packets bypassed due to a receive queue full. |
| cisco_ftd_disk_total_used | Bytes | The total space used on the device disk. |
| cisco_ftd_disk_used_percentage | % | The percent of disk space used by different partitions. |
| cisco_ftd_critical_process_restart_count | count | Restart count of each critical processes. |
| cisco_ftd_critical_process_cpu_util | % | Cpu utilization of each critical process. |
| cisco_ftd_critical_process_status | The status of critical processes | |
| cisco_ftd_critical_process_used_mem | Bytes | The memory used for each critical process |
| cisco_ftd_critical_process_uptime | s | The uptime of each critical process. |
| cisco_ftd_connection_in_use | count | Shows the number of connections in use |
| cisco_ftd_connection_most_used | count | Shows the maximum number of simultaneous connections. |
| cisco_ftd_cps_udp | count | The connections-per-second for UDP connection types. |
| cisco_ftd_cps_tcp | count | The connections-per-second for TCP connection types. |
| cisco_ftd_interface_drop_packets | count | The number of packets dropped. |
| cisco_ftd_interface_input_bytes | Bytes | The total incoming bytes. |
| cisco_ftd_interface_input_packets | count | The total incoming packets. |
| cisco_ftd_interface_output_bytes | Bytes | The total outgoing bytes. |
| cisco_ftd_interface_output_packets | count | The total outgoing packets. |
Risks, Limitations & Assumptions
- As of now the application only supports discovery and monitoring for FTDs managed by FMC or FDM.
- Application can handle Critical/Recovery failure notifications for below two cases when user enables App Failure Notifications in configuration:
- Connectivity Exception (ConnectTimeoutException, HttpHostConnectException, UnknownHostException)
- Authentication Exception (UnauthorizedException)
- Application will not send any duplicate/repeat failure alert notification until the already existed critical alert is recovered.
- Application cannot control monitoring pause/resume actions based on above alerts.
- Metrics can be used to monitor FTD resources and can generate alerts based on the threshold values.
- Event/Alert polling will start only if the user enables Event/Alert Polling in configuration.
- Possible values of Event/Alert Severity filter configuration property are kWarning, kCritical, kInfo.
- OpsRamp has given sample mappings to map FTD Severity with OpsRamp Severities as part of the Event/Alert Severity Mapping configuration file. You can modify them as per their use case at any point of time from the SDK application configuration page. Possible OpsRamp Severities are Critical, Warning, Ok, Info.
- No support of showing activity log and applied time.
- No support for the option to get Latest snapshot metric.
- Interfaces under FTD are represented as Network devices in OpsRamp.